Explain Different Security and Integrity Threats to the Database
Common methods include ransomware phishing attacks and hacking. Spyware is another data security threat that will find its way to your system through software installation.

How To Store A Password In The Database Cryptography Encryption Algorithms Security Application
Data integrity and data security are two different aspects that make sure the usability of data is preserved all the time.

. Virtual New Orleans LA June 12-15 2022. Human Errors Manual data entry increases the chances of errors duplications or deletion. For everyday Internet users computer viruses are one of the.
Dangers for Databases. The CIA criteria is one that most of the organizations and companies use in instances where they have installed a new application creates a database or. These listed circumstances mostly signify the areas in which the organization should focus on reducing the risk that is the chance of incurring loss or damage to data within a database.
A weakness in any information system component. Loss of data privacy. Like Trojans spyware can also be used to access sensitive information and even alter some of the data on your system.
Threats to the database You will build your security skills from two directions. Loss of confidentiality or secrecy. The CIA Confidentiality Integrity and Availability is a security model that is designed to act as a guide for information security policies within the premises of an organization or company.
Hire the best HR. Common threats that can alter the state of data integrity include. Free software is particularly to blame for the growth and infiltration of spyware.
To help achieve data security you need to minimize the. Data security is not the same as data integrity. Entity Integrity - This is related to the concept of primary keys.
Data integrity can be compromised several ways. The most common network security threats. Several factors impact the integrity of the data stored in a database including.
Database security encompasses tools processes and methodologies which establish security inside a database environment. To grow evolve and inspire we must engage in continuous learning. Here are a number of the most known causes and types of database security cyber threats.
Outsider or external threats are those that come from outside of the organization and usually are carried out by hacktivists other countries and even competition. Data Integrity Violation 22. There are different types of encryption algorithm such as AES MD5 and SHA 1 which are used to encrypt and decrypt the all types of sensitive data.
One is from the appre-ciation and awareness of changing threats and the other from the technical remedies to them. Given below are some database security threats. Loss of data integrity.
Data integrity in the database is the correctness consistency and completeness of data. Here are the most common security threats examples. Many software vulnerabilities misconfigurations or patterns of misuse or carelessness could result in breaches.
An additional element of integrity is the need to protect the. All tables should have their own primary keys which should uniquely identify a row and not be NULL. Categories of Security Threats 24.
Encryption is one of the most effective types of database security which protect your database from unauthorized access during storing and transmission over the internet. Threat to a database may be intentional or accidental. Categories of Security Vulnerabilities 23.
Credential Threats Employing substandard password management and authentication methods can allow identity theft brute force attacks and social engineering schemes such as phishing. Human error transfer errors bugs and viruses hacking cyber-threats compromised hardware and physical compromise to devices. Data integrity is enforced using the following three integrity constraints.
Data Integrity Threats Data integrity can be compromised through human error or worse yet through malicious acts. Weve all heard about them and we all have our fears. For example in a data breach that compromises integrity a hacker may seize data and modify it before sending it on to the intended recipient.
THREATS to security and integrity A threat is any situation event or personnel that will adversely effect the database security and smooth and efficient functioning of the organization. Theres no cause we cant effect when we come together as one HR. Some security controls designed to maintain the integrity of information include.
Data integrity refers to whether or not there are errors in your data like if its valid and accurate. Weve come a long way from Elk Cloner the 1982 Apple virus created by a secondary. Here are 10 data threats and how to build up your defences around them.
Data thats accidentally altered during the transfer from one device to another for example can be compromised or even destroyed by hackers. Main difference between integrity and security is that integrity deals with the validity of data while security deals with protection of data. Often the entered data fails to follow the apt protocol or the mistakes in the manual entry can extend to the execution of processes hence corrupting the results.
The challenges of the security program are to ensure that data is maintained in the state that is expected by the users. Data security is necessary to ensure that no one can access or change the information without authorization while data integrity means that its accurate. Data tampering Eavesdropping and data theft.
Backup and recovery procedures. Its worth noting that the security solutions can target multiple threats so dont limit yourself to trying one of them if you suspect a single culprit such as a virus. It can help ensure that any changes are intended and correctly applied.
Data security threats can be divided into insider and outsider threats. Loss of availability of data. Referential Integrity - This is related to the.
A security violation or attack that can happen any time because of a security vulnerability. Although the security program cannot improve the accuracy of the data that is put into the system by users. Dangers for Databases Security vulnerability.
Forgotten databases or new ones that the security team does not know about can be a serious database security and integrity threat.

The Overview Of Database Security Threats Solutions Traditional And Machine Learning

Database Security All You Need To Know In 5 Easy Points Jigsaw Academy

Describe One 1 It Position That You Currently Hold Or Would Like To Hold In The Future Next Explain Wh Bring Your Own Device Risk Management Administration

مزایای داشتن فروشگاه اینترنتی Integrity Zoho Online Reputation

Pdf Database Security Threats Prevention

Software Defined Security Cloudpassage Cloud Services Cloud Computing Risk Management

Database Security Databasse Security Control Tools And Benefits
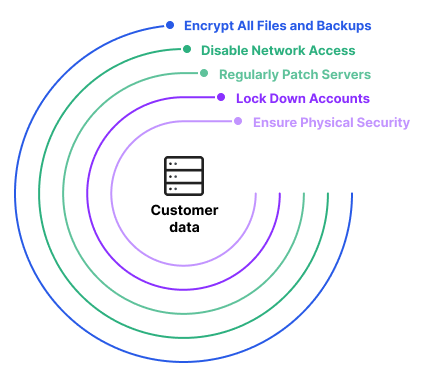
What Is Database Security Threats Best Practices Imperva
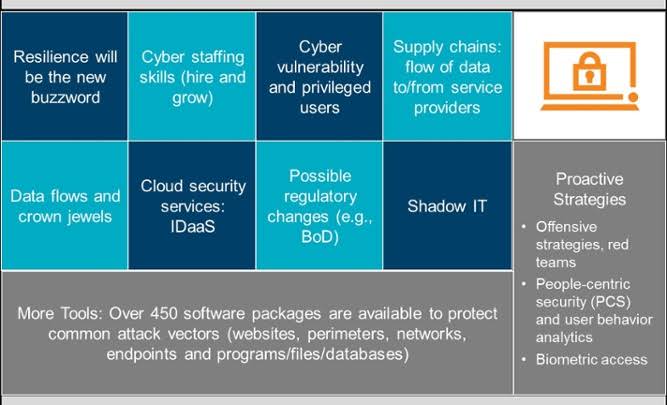
Yuk Intip 10 Peran Audit Internal Dalam Dunia Cyber Security Proxsisgroup

Pin On News Office 365 Azure And Sharepoint
Pdf A Survey Of Mobile Database Security Threats And Solutions For It
Pdf A Review Of Database Security Concepts Risks And Problems

Properties Of Database Security Download Scientific Diagram

Api Architecture Cheatsheet In 2022

Pdf Database Security Attacks And Control Methods
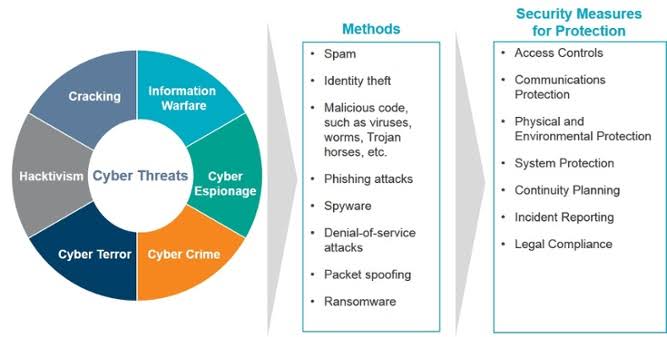
Yuk Intip 10 Peran Audit Internal Dalam Dunia Cyber Security Proxsisgroup

Rest Api Security Vulnerabilities Dzone Encryption Algorithms Vulnerability Security

Learn What Are The Most Important Api Security Threats Engineering Leaders Should Be Aware Of And Steps You Can Take To Prevent The Security Threat Ddos Attack

8 Critical Database Security Best Practices To Keep Your Data Safe
Comments
Post a Comment